(Originally published on Sucuri’s blog June 9, 2020)
Website defacement is the most obvious sign of a hack. In these cases, bad actors who have gained access to an environment leave their mark through digital vandalism. For website owners, it means trying to access your homepage, only to find all of the code and content you’ve worked on replaced with something like this:
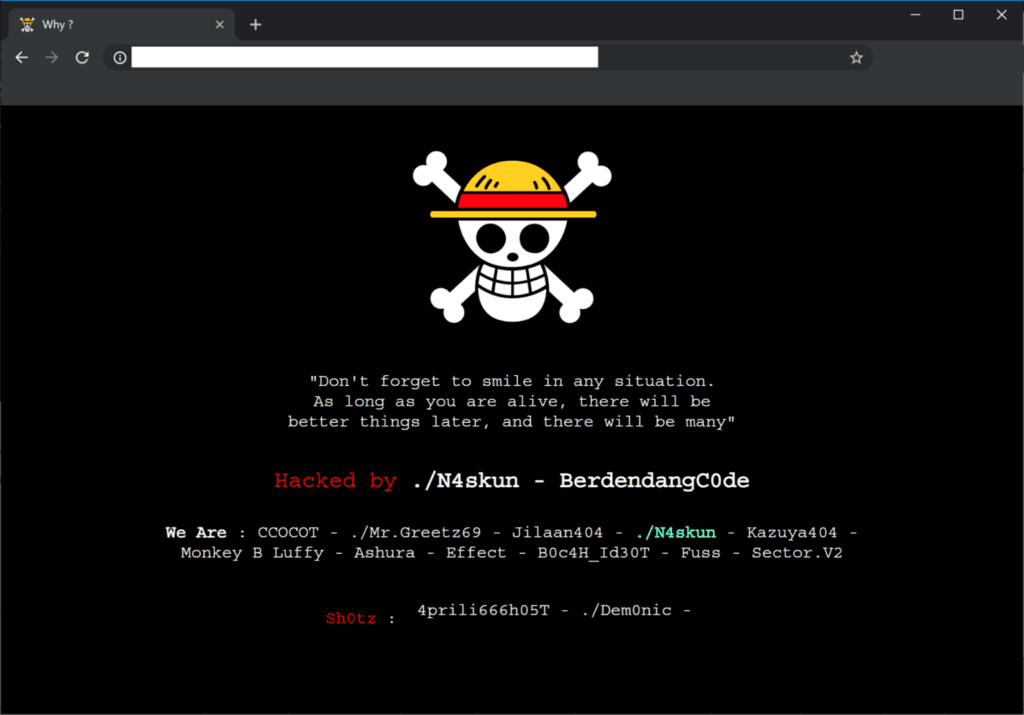
While many website hacks are designed for financial gain, website defacements are a different kind of hack. In these cases, the hackers are just trying to share a message. In the above example, it was just to flaunt their skills and leave a “calling card” to gain a bit of street cred. But defacements can also be focused on some political, religious or ideological goal.
Regardless of the intent, finding your site with a “hacked by” message is something you’ll want to get resolved as soon as possible.
How do hackers deface websites?
Hackers deface websites by gaining unauthorized access to an environment. The methods can vary, but popular methods of entry include vulnerabilities in third-party plugins and stolen login credentials. Hackers who discover these vulnerabilities can gain edit access to a website and make whatever changes they see fit.
Just as the methods of defacement will vary, the depth of the attack can also vary. It may be as simple as the website’s index.php file being modified. This kind of hack can be fixed by simply replacing the hacked index.php file with a clean copy.
But hackers may also go a bit deeper in their defacement and alter important system files as well. In this case, you may be looking at a more difficult cleanup.
Examples of website defacements
Website defacements tend to look like… well, what you’d expect from a hacker defacement. You can often expect scary imagery like a skull and crossbones, biohazard symbols, or some other fear-inducing sight.
Apart from imagery, hackers will also take credit for the attack by leaving their mark or “signatures.” Most common hacker signatures are usually pretty generic with wording such as “hacked by”, “pwnd by,” “defaced by,” “Been Hacked By,” “YOU GOT HACKED,” and other combinations.
Some hackers don’t like getting creative with the imagery and will just go with plain text defacements, like the one seen above. The fortunate part about signatures usually being generic is that it will make it easier to detect during a malware removal process.
There are some common names of hacker groups in signatures. Because the nature of these attacks is publicity, we’ve decided not to provide any of the most recent groups’ names. But just for a stroll down memory lane, here are a few of the top hacked by signatures from years past.
- hacked by imam
- hacked by mister spy && souheyel && tayebjaaba
- hacked by ng689skw
- hacked by red virus
- hacked by anonymous
What are the consequences of website defacements?
The consequences of website defacements are the same as any other hack, just much more obvious. Visitor trust will be immediately diminished when users visit a page that is clearly displaying signs of being hacked.
And the longer you allow your website to display the defacement, the worse it will get. An outward-facing website compromise will likely result in a blacklist from Google and other search engines. This means your site will stop ranking in search results. Getting off of a blacklist can be difficult, which is why you’ll want to clean up any website defacements as soon as possible.
How to Recover a Defaced Website
If you’ve been keeping regular backups, recovering a defaced website is easy. Simply restore your site back to its original form from the last uncompromised backup. But if you do not have a backup, it will require a bit more work.
In a case where a backup restoration is not possible, you will want to:
- Log into your server via SFTP or SSH.
- Make a backup of your site in its current state.
- Identify any recently changed files on the server and confirm any changes with users who might have made them.
- Restore suspicious CMS system files with fresh copies from a stock installation.
- For any custom or premium files, open the file with a text editor to remove any suspicious code.
- Test to verify the site is still operational after changes.
Once the site is back to its original state, you’ll want to take a few more precautions to ensure that hackers can not gain access again.
- Change all passwords – If a user account was compromised during the hack, you’ll want to make sure the attackers do not have access. Changing the password will help. Use a password manager like LastPass, KeePass, or 1Password to generate and store secure passwords.
- Update all themes and plugins – Third-party CMS plugins and themes are the most likely source of compromise for most websites. Keeping them up to date will ensure you are running the most secure versions. You can also use a security solution with virtual patching to run any plugins with known vulnerabilities.
- Practice the principle of least-privilege – Check into your user settings and only give users the bare minimum of access they need to do their work. This will limit the chances of hackers being able to gain access to deface your website.
But if you are feeling at all uncomfortable about cleaning up a defaced website on your own, don’t worry. Help is available. Sucuri offers website security solutions that can clean your site and protect you from any future website defacements.